
Trusted Computing: The COTS Perspective Series
This is the first of an ongoing series of papers that will address the use of open standards-based Commercial-Off-The-Shelf (COTS) technologies to address Trusted Computing requirements in deployable embedded systems for aerospace and defense applications. First, let's define what we mean when we talk about Trusted Computing.
The Elements of Trusted Computing
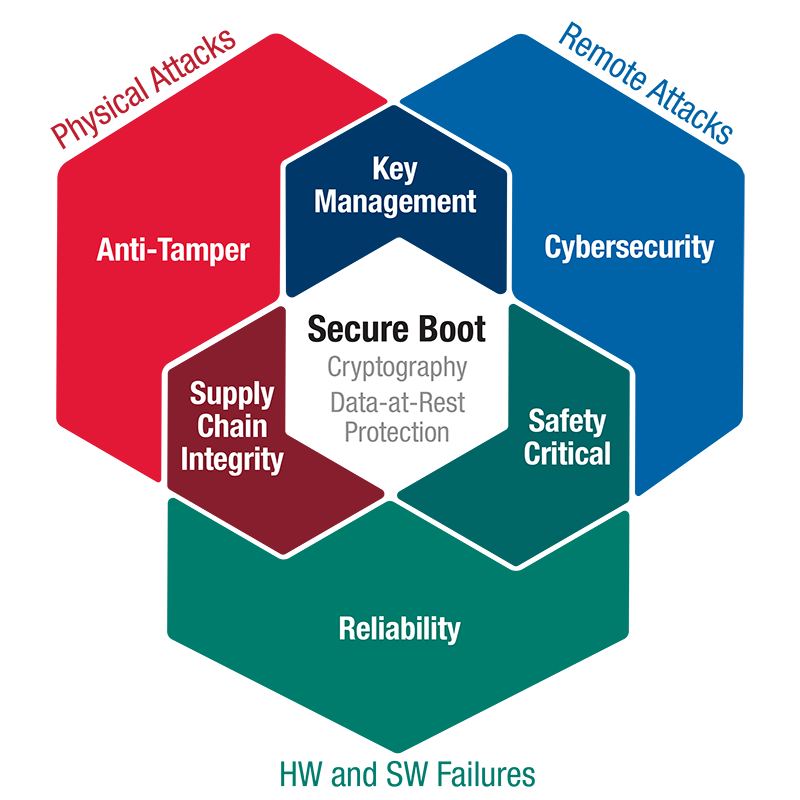
The term Trusted Computing refers to the technologies and techniques that protect embedded electronics modules and integrated systems from physical and remote attacks and from hardware and software failures. Through Anti-Tamper methodologies and avionics Safety Certifiability processes, Trusted Computing also ensures that a system will only execute what is intended and nothing else.
In the aerospace and defense market, solutions based on embedded hardware are frequently used in critical applications that may involve sensitive and classified information. The goal of all Trusted Computing activities is to enable the operation of these systems with complete confidence that they are secure and uncompromised. Trusted Computing also delivers confidence that any critical data or IP will not benefit our adversaries if the hardware falls into enemy hands.
Anti-Tamper defines the set of solutions to protect against Physical Attacks on the system. Cybersecurity defines those protections fielded against Remote Attacks. System Reliability results from activities designed to mitigate hardware and software failures. Approaches for providing Trusted Computing for Anti-Tamper, Cybersecurity and Reliability can intersect in various ways.
Download the white paper to learn more.
- Trusted Computing
- Anti-Tamper
- Cybersecurity
- Reliability
- Supply Chain Integrity
- Safety Certifiability