
Trusted Computing is a broad concept that encompasses different security techniques and technologies. As a result, the phrase is used in many different ways. Trusted Computing ensures:
- That the computer will consistently behave in expected ways, and that the computer hardware and software will enforce those behaviors
- That hardware and software architectures, designs, tools, and algorithms will ensure the validity and confidentiality of computing results
The second definition best captures the breadth of Trusted Computing. It reflects the fact that every element in a solution plays a role in ensuring that the system behaves in the way it is expected to behave and that the data is always accurate and available and provided to only authorized recipients. Essentially, security must be implemented at every layer of each solution to create a system that can be fully trusted.
No single layer of security is ever foolproof. Each solution must be built so that if one layer of security is broken or compromised, there are other layers that continue providing protection. Picture slices of Swiss cheese layered on top of one another. Each slice may have some holes, but by layering the slices, holes can be covered by other layers with non-overlapping holes. Or, picture an onion, where the core is still protected even if one or more outer layers is peeled away. With this approach, one compromised layer doesn’t compromise the entire solution.
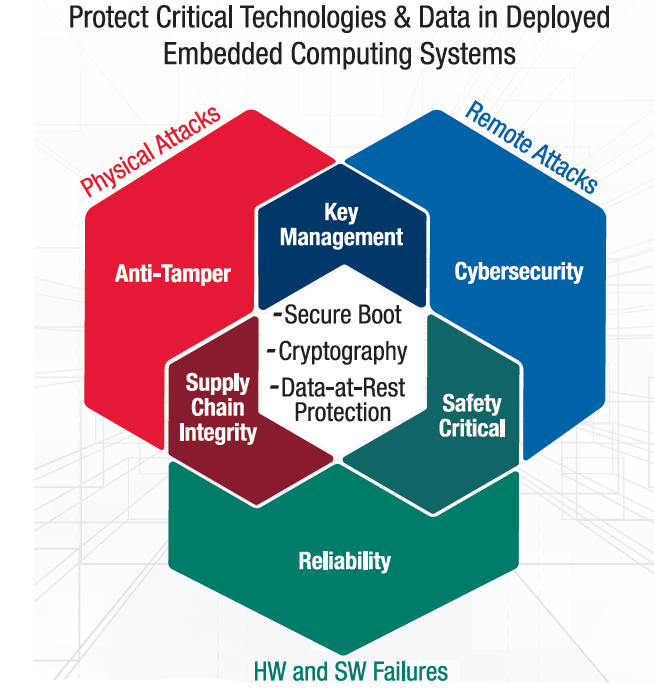
Figure 1: The Layered Approach to Trusted Computing
Within Trusted Computing, various techniques are used to help protect each layer and enable the capabilities described in the previous section. It’s the combination of techniques and capabilities that enables the security at each layer. For example, hash techniques may be used to identify data that has been changed to protect the integrity of the data, but the hash does not protect the confidentiality of the data. Instead, cryptography techniques that scramble data are needed to protect confidentiality whenever data is transmitted.
In many cases, a vendor will not, or cannot, describe exactly how data is being protected. For example, there are anti-jamming techniques that counter GPS signal jamming attempts, but revealing how that is done would put important information into the hands of adversaries.
Learn more about Trusted Computing, download our white paper, "The Many Faces of Trusted Computing".