
Manned and unmanned aircraft like the Orion, Poseidon, Global Hawk, Triton, AWACS, and Hawkeye gather a massive volume of sensor data during intelligence, surveillance, and reconnaissance (ISR) missions. In a tactical, fast-moving situation, the collected ISR data must be analyzed quickly to provide decision-makers with the crucial information required. To facilitate faster processing, the analysis of this critical data is increasingly being handled by data-processing systems embedded into the aircraft themselves as part of a tactical edge computing process. With the data close at hand, latency and downtime are reduced and operators can extract the necessary tactical information as quickly as possible for any mission requirement.

Figure 1: ISR Aircraft Example
Unfortunately, processing the data at the edge creates new risks. If the aircraft is downed or lost, the data may become available to an adversary. Data passed on for further analysis before storage may also be vulnerable. But these risks can be mitigated by protecting the data at rest (DAR) with advanced encryption.
Edge Computing
In the commercial and industrial worlds, the movement of data processing to the tactical edge is known as edge computing. The move to edge computing is being driven by several factors caused by the prevalence of the Internet of Things (IoT) devices—bandwidth limitations, latency issues, and unpredictable network disruptions.
There are millions of commercial IoT sensors now. Think about your home, for instance. Most of us have smart TVs that are connected to the internet and streaming services. Our smart thermostats are connected to the internet and controlled by our phones. Even our refrigerators are smart now. Similarly, industrial applications have many IoT sensors monitoring manufacturing or refining processes—temperature, salinity, viscosity, thickness, etc.
These millions of IoT sensors generate incredible amounts of data. Not all of the data requires permanent storage. Edge controllers sift through the data and reduce it to a more valuable, refined subset. If the data requires further refinement or analysis, it goes to more powerful computers in the fog layer. Once the data has been processed, it goes to the cloud for storage and further analysis. Some edge computer applications may bypass the fog layer and send the data straight to the cloud layer for storage and analysis (Figure 1 and Figure 2).
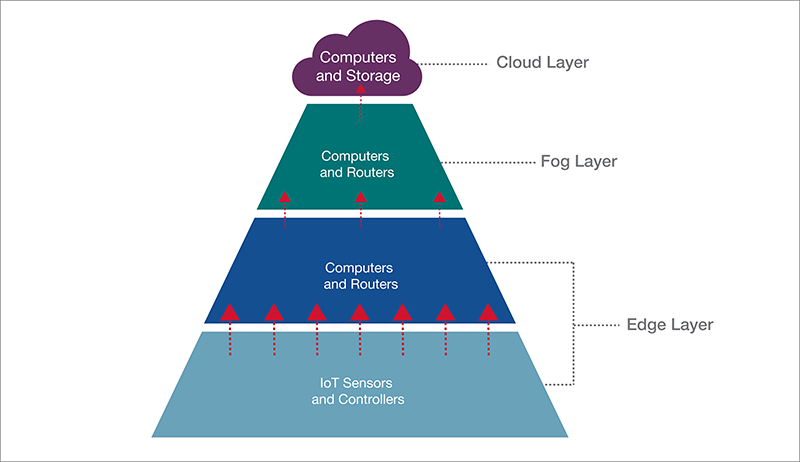
Figure 2: Commercial Edge, Fog, and Cloud Computing
Military Edge Computing Architecture
The military is moving towards tactical edge computing for the same reasons. Obviously, an aircraft cannot be wired directly to a fog layer or cloud layer. The military may rely on radio, microwave, or satellite communications links to transfer data from sensors, which have bandwidth limitations and latency issues. These wireless network connections may also be disrupted by system malfunctions or by the willful acts of an adversary.
For an airborne ISR application, the closest place to the tactical edge is on the aircraft itself. Some of the sensor data can be analyzed onboard the aircraft during a mission. This is the most efficient method to extract the key information and avoid bandwidth and latency issues and network disruptions.
The deployed military networks on ISR aircraft are, by design, mobile. So, size, weight, and power (SWaP) are very important. Thus, the deployed computers, sensors, and other electronic equipment must be compact, lightweight, and power-efficient, driving airborne computers to be smaller and lighter, instead of more powerful (like in a cloud data center). Of course, the ideal would be both small and powerful. But this does not always work out.
On ISR aircraft, this local sensor data processing is performed by digital signal processors (DSP), single-board computers (SBC), and other similar processors. Ethernet networks in modern aircraft facilitate the transfer of information between sensors, computers, and network attached storage (NAS) devices. Sensors collect data and either send it to a central NAS for storage or directly to a computer for processing. That NAS is used by all the airborne-edge computers to retrieve sensor data for analysis. Once analyzed by the edge computers, this reduced and refined sensor data can be sent to displays for human interaction and decision-making.
In this process, the edge layer is the aircraft itself. The data at rest that resides on the network attached storage on the aircraft is likely classified or top-secret level data, which would be valuable to an adversary if the aircraft is shot down or lost. With this risk in mind, the data at rest must be protected.
The next best place for data analysis is a tactical operation center or local ground station. This layer is equivalent to the commercial fog layer. To be analyzed and reduced further by more powerful and larger fog computers, the data at rest must be removed from the network attached storage on the aircraft and taken to a ground station. Removable memory cartridges (RMC) are used to transfer data at rest from the aircraft to the ground station. If encrypted properly, these RMC are considered unclassified during transport. The encryption method used on the aircraft must also be used at the ground station to facilitate decryption.
This transfer of sensor data brings in an element of risk. Adversaries may intercept the RMC and try to take advantage of the data. Data at rest is also at risk while on the ground-station network. Sophisticated individuals and nation-states will seek to access this data. These continual efforts to obtain classified data are known as advanced persistent threats (APT). So, how can the data at rest be protected?
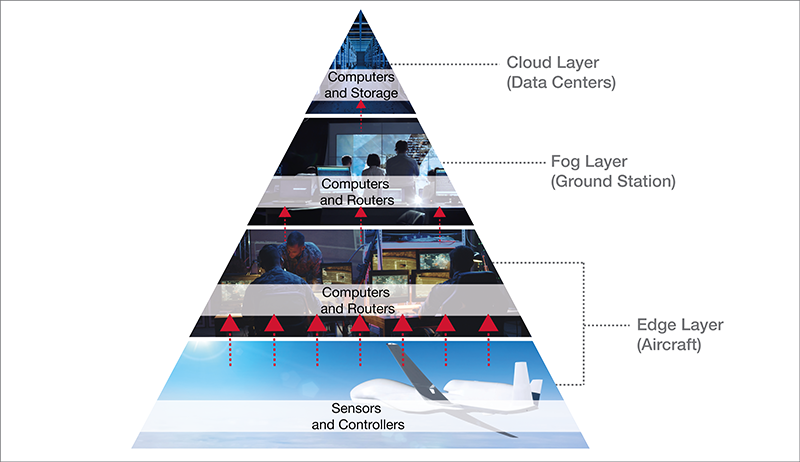
Figure 3: Military ISR Aircraft Architecture Example
Protecting Data at Rest
In military-deployed applications, classified data at rest is encrypted so that APT cannot easily access or use the data at rest if the aircraft or RMC were lost or captured. Two methods of approved encryption are being used by the U.S. military today: Commercial Solutions for Classified (CSfC) and Type 1 (or High Assurance). Each encryption approach has its advantages. An example of a CSfC-approved network attached storage device is shown in Figure 4. An example of a network attached storage with NSA-approved Type 1 encryption is shown in Figure 5.
When bandwidth and networks allow, the reduced data set is sent by the ground station to the cloud layer. The military cloud is much like the commercial cloud in many respects—it has powerful computers and massive storage. The cloud is used for long-term storage or archiving of important data and for strategic analysis. Data from many ground stations will be collected and analyzed.

Figure 4: DTS1 Network Attached Storage (NAS)

Figure 5: Unattended Network Storage with Type 1 Encryption
Summary
Edge computing is increasingly being used in the commercial and industrial worlds to resolve bandwidth limitations, latency issues, and networks disruptions. Tactical edge computing is accomplishing the same way in the military world. With computing moving to the tactical edge, network attached storage devices play an important role on the aircraft and during data at rest transfer. If the vehicle is lost or captured, the data at rest is protected with approved encryption methods. Network attached storage devices can use RMC to transfer data quickly and safely from the ISR aircraft to the ground station for further analysis. Expect that this trend of pushing computing closer to the tactical edge will continue for deployed military applications.
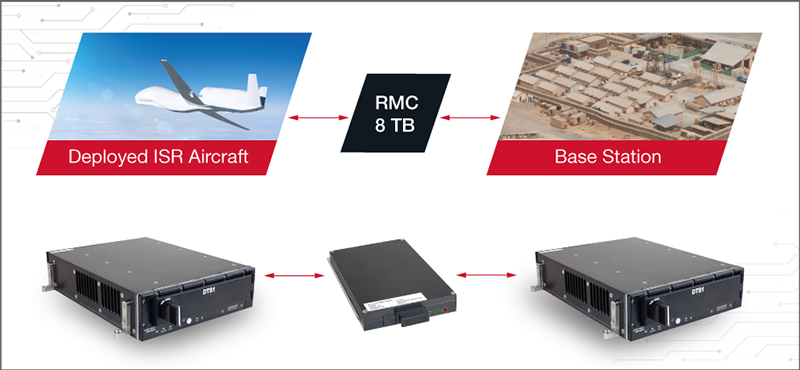
Figure 6 - Data Transfer from Edge Layer to Fog Layer