
What is CSfC?
Commercial Solutions for Classified (CSfC) is an integral part of the National Security Agency (NSA)’s strategy to deliver secure cybersecurity solutions. The program leverages commercial encryption technologies, such as those employed in cars, mobile phones, tablets, and home security systems, to deliver cybersecurity solutions for classified applications quickly.
How CSfC Prescribes a Layered Approach to Data at Rest Encryption
Data at rest (DAR) can be threatened from four different vectors, some internal and some external. In deployed DAR applications (e.g., planes, helicopters, unmanned underwater vehicles, ground vehicles), vehicles may be lost during a mission. The data at rest can also be lost during transport from the deployed vehicle back and forth to the ground station. Once mission data has been safely downloaded and stored on a network, it is still at risk to relentless hackers (nation-state and independent) and unknown internal bad actors with malicious agendas.
CSfC is founded on the principle that properly configured, layered solutions can provide adequate protection of classified data in various applications. Two layers of data at rest encryption are required to be fielded as a solution.
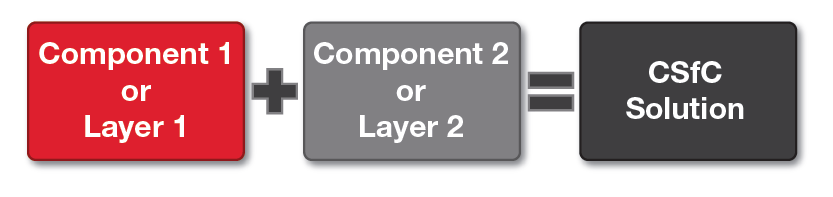
Figure 1 A CSfC solution requires two layers of DAR encryption
When properly implemented, a single layer of data at rest encryption from the Commercial National Security Algorithm (CNSA) Suite is sufficient to protect classified data; however, two layers are used to mitigate risks due to a failure in one of the layers. Such a failure may result from accidental misconfiguration, operator error, or malicious exploitation of an implementation vulnerability – any of these can result in the exposure of classified data at rest. The use of multiple layers, implemented with components meeting the CSfC vendor diversity requirements, reduces the likelihood that a single vulnerability can be exploited to reveal protected information.
If one of the encryption layers is compromised or fails in some way, the second layer can still provide the encryption to safeguard the classified data. If both layers are compromised or simultaneously fail, then it is possible the classified data will be readable by an adversary. The goal of the data at rest encryption solution is to provide redundant protection that either minimizes the possibility of both layers failing at the same time or requires an adversary to defeat both mechanisms. Given enough time, any encryption system may be defeated. But with two layers, that task becomes significantly more difficult.
What is CSfC Terminology?
Terminology specific to CSfC can be confusing. Gaining a basic understanding of the vocabulary used by the program is necessary before diving deeper into program specifics.
Component: a CSfC product developed by a COTS vendor, tested by an approved laboratory, certified by the National Information Assurance Partnership (NIAP), and approved by NSA. Typically a component comprises one layer of a two-layer solution (refer back to Figure 1). The only acceptable components are:
- Software full disk encryption (SWFDE)
- Hardware full disk encryption (HWFDE)
- File encryption (FE)
- Platform encryption (PE)
Solution: two independent layers of encryption products (components). Solutions must be composed of a combination of two of the component types:
- SF = SWFDE + FE
- PF = PE + FE
- HF = HWFDE + FE
- HS = HWFDE + SWFDE
- HH = HWFDE + HWFDE (proposed in draft DAR CP 4.8 as of this writing)
End User Device (EUD): refers to anything employed with two layers of CSfC data at rest protection. Thus an EUD is a data at rest protected system. Terms like system, data at rest solution, or device are equivalent.
Capability Package (CP): a product-neutral document that describes system-level solution frameworks, documenting security and configuration requirements for customers and/or integrators. The set of guidance provided by the NSA describes recommended approaches to provide architectures and configuration requirements that empower IA customers to implement secure solutions using independent, layered COTS components to protect classified information. This package will point to potential products that can be used as part of this solution. CPs are used by COTS vendors, integrators, and end customers alike.
Trusted Integrator (TI): persons or companies that the NSA has vetted to architect, design, integrate, test, document, field, and support a solution. While not required to use a trusted integrator, the use of a TI can be a risk mitigation factor.
Protection Profile (PP): a requirements document used as part of the certification process according to the Common Criteria. The generic form of a security target, the PP is typically created by a user or user community and provides an implementation-independent specification for information assurance security requirements.
Collaborative Protection Profiles (cPP): a PP that has been reviewed and accepted by the international Common Criteria community.
Commercial National Security Algorithm (CNSA): a set of commercial algorithms capable of protecting data through Top Secret level (previously known as Suite B).
Full Disk Encryption (FDE): the process of encrypting all of the data on a hard drive. Sometimes referred to as whole disk encryption, FDE encrypts all data (with certain exceptions) on the storage device and permits access to the data only after successful authorization to the FDE solution.
Software Full Disk Encryption (SWFDE): FDE accomplished with software (SW). Software like Linux’s LUKS is an example of SWFDE.
Hardware Full Disk Encryption (HWFDE): FDE accomplished with hardware (HW). An ASIC like the eNova MX-256 is an example of HWFDE.
Continue reading the Commercial Solutions for Classified (CSfC) white paper.