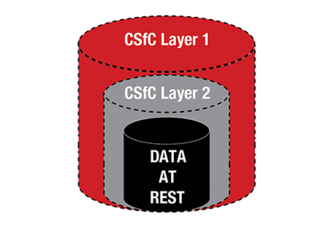
Commercial Solutions for Classified (CSfC) is an important part of NSA’s commercial cybersecurity strategy to deliver secure solutions that leverage commercial technologies and products to deliver cybersecurity solutions quickly. The CSfC program is founded on the principle that properly configured, layered solutions can provide adequate protection of classified data in various applications. NSA has developed, approved, and published solution-level specifications called Capability Packages (CPs) and works with technical communities from across industry, governments, and academia to develop and publish product-level requirements in U.S. Government Protection Profiles (PPs).
Curtiss-Wright offers CSfC solutions in both the data-at-rest (DAR) and data-in-transit (DIT) CSfC categories. These solutions reflect Curtiss-Wright’s knowledge, experience and commitment to the CSfC Program. Information sharing and data storage is critical to ensure mission success. Curtiss-Wright is committed to provide CSfC solutions that are trusted and proven.
What is Commercial Solutions for Classified?
Want to know all things CSfC? This white paper is a great place to start.
The benefits of the NSA's CSfC program
The CSfC program enables organizations to transmit classified information using commercial-grade encryption solutions (when appropriately tested, certified and configured), eliminating the need for expensive, difficult-to-use classified equipment.
Providing such benefits as:
- Enabling entirely new classes of wireless access to classified networks for warfighting
- Enabling U.S. coalition partners to access classified information without taking possession of controlled cryptographic items (CCI)
- Significantly reduces equipment costs and simplifies key management
- Simplifies equipment handling/security procedures
The NSA now allows classified information to be transmitted on wired and wireless connections, even over public and partner networks by using two sets of encryption technologies (such as Cisco and Aruba VPNs), one layered inside the other. The NSA has also approved combinations of solutions that include a layer of VPN combined with encryption provided by Wi-Fi, TLS or MACsec, following specific guidelines.
Secure Wireless Communication Supporting Vehicle-to-Vehicle and Vehicle-to-EUD for Mounted and Dismounted Connectivity
The goal of Secure Wireless Communications is to provide controlled access to classified or controlled unclassified information (CUI) over any RF transport in the field - between vehicles and end-users alike.
Secure Wireless Solutions for Tactical, Expeditionary, and Deployable Communications
PacStar communications solution products, technical expertise, integration, test, and certification experience in deployed and fixed networking systems based on commercial-off-the-shelf (COTS) equipment provide our customers with a one-stop-shop for CSfC solutions.
Common Criteria is a standard administered by the International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC). It serves as a framework that allows products to be evaluated against a defined Security Target (ST) and Security Functional Requirements (SFR). Normally, products will pull much of their ST from an already defined Protection Profile (PP) for a given set of products. Products are then evaluated against their defined ST and SFR at an independent lab.
How is NSA Type 1 Encryption different than NSA Commercial Solutions for Classified Encryption?
This white paper discusses over a dozen factors will be discussed to compare the two encryption options. The analysis of those factors will be from a United States vendor or developer perspective. For instance, the export factor, that will be explored later, will refer to export from the US to other countries.
 Learn More
Learn More
 Learn More
Learn More
 Learn More
Learn More